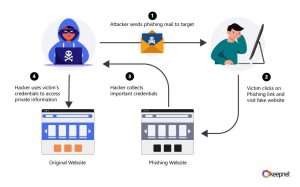
Hackers Are Tricking Users Into Installing Malware: Here’s How It Works
The Latest Scam: “Fix Your PC” Pop-Ups That Install Malware You’re browsing the web when suddenly a pop-up appears. “Critical…
Top 11 Must-Have SysAdmin Tools in 2025: Boost Efficiency & Security
SysAdmins in 2025: Overworked, Underappreciated, and in Need of Better Tools Let’s be real, SysAdmins have one of the toughest…
Hackers Can Now Bypass Key Web Security: Here’s How They Do It
The Security Measure You Trust Might Not Be Enough We’ve all been there you install what you think is an…
Hackers Hijack Windows Task Scheduler to Install Persistent Malware
The Silent Invasion: How Malware Lives in Your System Undetected We’ve all heard about computer viruses, but modern cyber threats…
16 Billion Passwords Leaked: The Largest Credential Spill in History: What You Need to Do Now
The Largest Password Leak in History This isn’t just another data breach. Security experts have uncovered what may be the…
Amatera Stealer: The Silent Data Thief Infecting Your Devices
The Rise of Amatera Stealer Imagine visiting a normal website, solving a simple CAPTCHA, and suddenly your passwords, credit cards,…
Academic Bait-and-Switch: The Sneaky Malware Hidden in Research Papers
The Email That Almost Fooled Me A few months ago, a colleague almost fell for one of these scams. He…
NIST’s New Zero Trust Guide: 19 Blueprints to Secure Your Network in 2025
Why Zero Trust Isn’t Just Another Buzzword Remember when companies relied on a single firewall and called it “security”? Those…
Crypto Devs Beware: How Weaponized npm and PyPI Packages Are Draining Wallets
The Silent War on Crypto Developers: Weaponized npm and PyPI Packages Exposed The cryptocurrency and blockchain space is no stranger…
Fog Ransomware’s New Playbook: How Hackers Are Weaponizing Pentesting Tools
Introduction: A New Era of Ransomware Attacks Ransomware isn’t what it used to be. Gone are the days when attackers…