The Hidden Cyber Threats Targeting Your Business And How to Stop Them
Imagine this: Hackers already have your employee’s login details. They’re selling them on the dark web for pennies, waiting for…
This is the Best Way to Stop Identity Theft Before It Happens?
Let’s be real identity theft isn’t just something that happens to “other people.” I used to think that way too,…
The Best VPNs for Students in 2025: Stay Safe Without Breaking the Bank
Let’s be real college life means living online. Between Zoom lectures, late-night study sessions at the library, and binge watching…
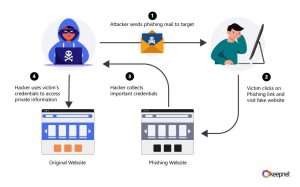
“Darcula” Phishing Scam Exposed: How Cybercriminals Stole 884,000 Credit Cards
The Rise of Darcula: A Cybercriminal Powerhouse Imagine getting a text from your bank warning about suspicious activity. You click…
How to Secure Your Email with DMARC, SPF, and DKIM (A Step-by-Step Guide)
Why Your Inbox is a Hacker’s Favorite Playground (And How to Fix It) Let’s be real email security sounds about…
Microsoft’s Passwordless Future: What It Means for You
For years, passwords have been the weakest link in online security. We forget them, reuse them, or fall for scams…
Dutch Institutions Face Relentless Cyberattacks from Pro-Russia Hacktivists
The Attacks: A Wave of Digital Disruption This week, the Netherlands found itself in the crosshairs of a persistent cyber…
The Cloud Security Crisis: Why 90% of Companies Are Under Attack (And How to Stay Safe)
If you thought moving to the cloud would make your business safer, think again. A staggering 90% of cybersecurity leaders…
The CISO’s Guide to Penetration Testing: How to Stay Ahead of Hackers
Let’s be honest cybersecurity isn’t getting any easier. Every day, hackers come up with new ways to break into systems,…
MTN Ghana Data Breach: What Happened, Who’s Affected, and What’s Next
So, What Actually Happened? Earlier this week, MTN Ghana dropped a press release confirming what many of us dread—a cybersecurity…