Why This Stuff Actually Matters
Let’s be real cybersecurity isn’t just about firewalls and antivirus anymore. If you’re a CISO or security lead, you’re juggling compliance headaches, boardroom skepticism, and the constant fear that tomorrow’s headline will be about your company’s data breach.
Frameworks exist to make this mess manageable. They’re like blueprints some are strict rulebooks, others are flexible guidelines. The trick? Knowing which one (or which mix) actually fits your business. Because let’s face it: no one has time for security theater.
Here’s the breakdown of the five frameworks that actually matter, stripped of the jargon.
1. NIST CSF: The Government’s Playbook (But Actually Useful)
The Gist:
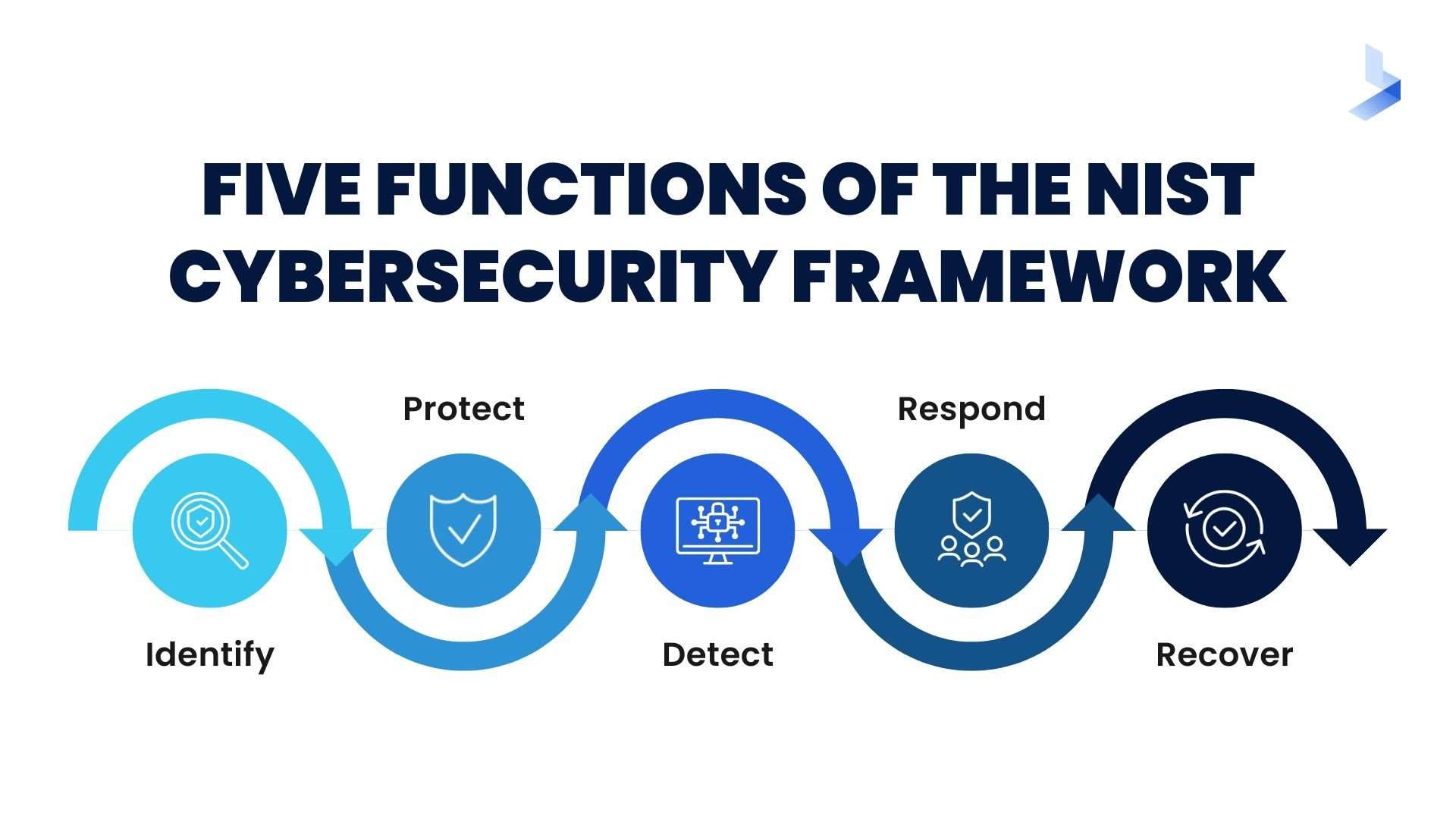
The National Institute of Standards and Technology (NIST) built this for critical infrastructure, but everyone uses it because it’s that adaptable. It’s built on five pillars:
-
Identify (What’s actually at risk?)
-
Protect (Basic defenses think access controls)
-
Detect (Catching hackers before they throw a party in your servers)
-
Respond (How not to panic during a breach)
-
Recover (Because things will go wrong)
Who It’s For:
-
Companies that need structure without suffocating rules
-
Industries drowning in regulations (healthcare, finance, energy)
The Real Talk:
NIST is like a security Swiss Army knife—useful everywhere, but you’ll still need other tools. It won’t give you step-by-step instructions, but it’ll keep you from missing the big stuff.
2. ISO 27001: The Gold Star for Security Nerds
The Gist:
This is the international standard for security management systems (ISMS). Translation: It’s a process, not just a checklist. You’ll document everything, get audited, and (if you pass) earn a shiny certification.
Who It’s For:
-
Global companies that need to prove they’re serious about security
-
SaaS and cloud providers dealing with paranoid enterprise clients
The Real Talk:
ISO 27001 is rigorous. Getting certified takes months, costs a small fortune, and involves more paperwork than a mortgage application. But if you need to win trust (or contracts), it’s worth it.
3. CIS Controls: The “Stop Getting Hacked” Checklist
The Gist:
The Center for Internet Security (CIS) distilled security down to 20 controls that stop ~85% of attacks. Things like:
-
MFA everywhere (because passwords alone are a joke)
-
Patching fast (unpatched systems are hacker candy)
-
Limiting admin access (not everyone needs the keys to the kingdom)
Who It’s For:
-
Small teams with limited resources
-
Companies that want quick, high-impact wins
The Real Talk:
This is the “stop bleeding first” approach. No fluff, just the stuff that actually prevents breaches.
4. SOC 2: The Trust Builder for Tech Companies
The Gist:
A compliance standard for service providers (think SaaS, cloud, MSPs). It’s all about proving you’re secure in five areas:
-
Security (duh)
-
Availability (your stuff stays online)
-
Confidentiality (data doesn’t leak)
-
Processing Integrity (no sketchy data handling)
-
Privacy (if you collect personal data)
Who It’s For:
-
Tech startups selling to big enterprises
-
Any company where “trust” is a sales pitch
The Real Talk:
SOC 2 is not a one-and-done deal. You’ll need annual audits (Type II is the real test). But if Walmart or Bank of America asks, “Are you SOC 2 compliant?” you’ll want to say yes.
5. PCI DSS: The Credit Card Police
The Gist:
If you handle credit card data, the Payment Card Industry (PCI) will make you comply with their 12 requirements. No exceptions.
Who It’s For:
-
E-commerce stores
-
Any business that processes payments
The Real Talk:
PCI DSS is not optional. Fail compliance, and you’ll face fines or worse lose the ability to process payments. It’s rigid, but it works.
How to Actually Pick One (Without Losing Your Mind)
Step 1: Figure Out What You’re Protecting
-
Customer data? ISO 27001 or SOC 2
-
Credit cards? PCI DSS
-
Just need basics? CIS Controls + NIST
Step 2: Know Your Audience
-
Selling to enterprises? They’ll demand SOC 2 or ISO 27001
-
In healthcare or finance? NIST + industry-specific rules
Step 3: Start Small, Then Scale
-
Pilot in one department before rolling out company-wide
-
Measure success (fewer incidents? Smoother audits?)
The Bottom Line
There’s no “perfect” framework just the one that fits your business today. The best security leaders mix and match, using NIST for strategy, CIS for quick wins, and ISO or SOC 2 for credibility.
Because at the end of the day, security isn’t about checkboxes. It’s about making sure your company doesn’t end up on the evening news.
Discover more from CyberAwareHub
Subscribe to get the latest posts sent to your email.